
What You Should Know About VPNs: A Practical Security Guide
In today’s connected world, the way we work and access information has changed significantly. Remote work, coffee shop meetings, and […]

In today’s connected world, the way we work and access information has changed significantly. Remote work, coffee shop meetings, and […]
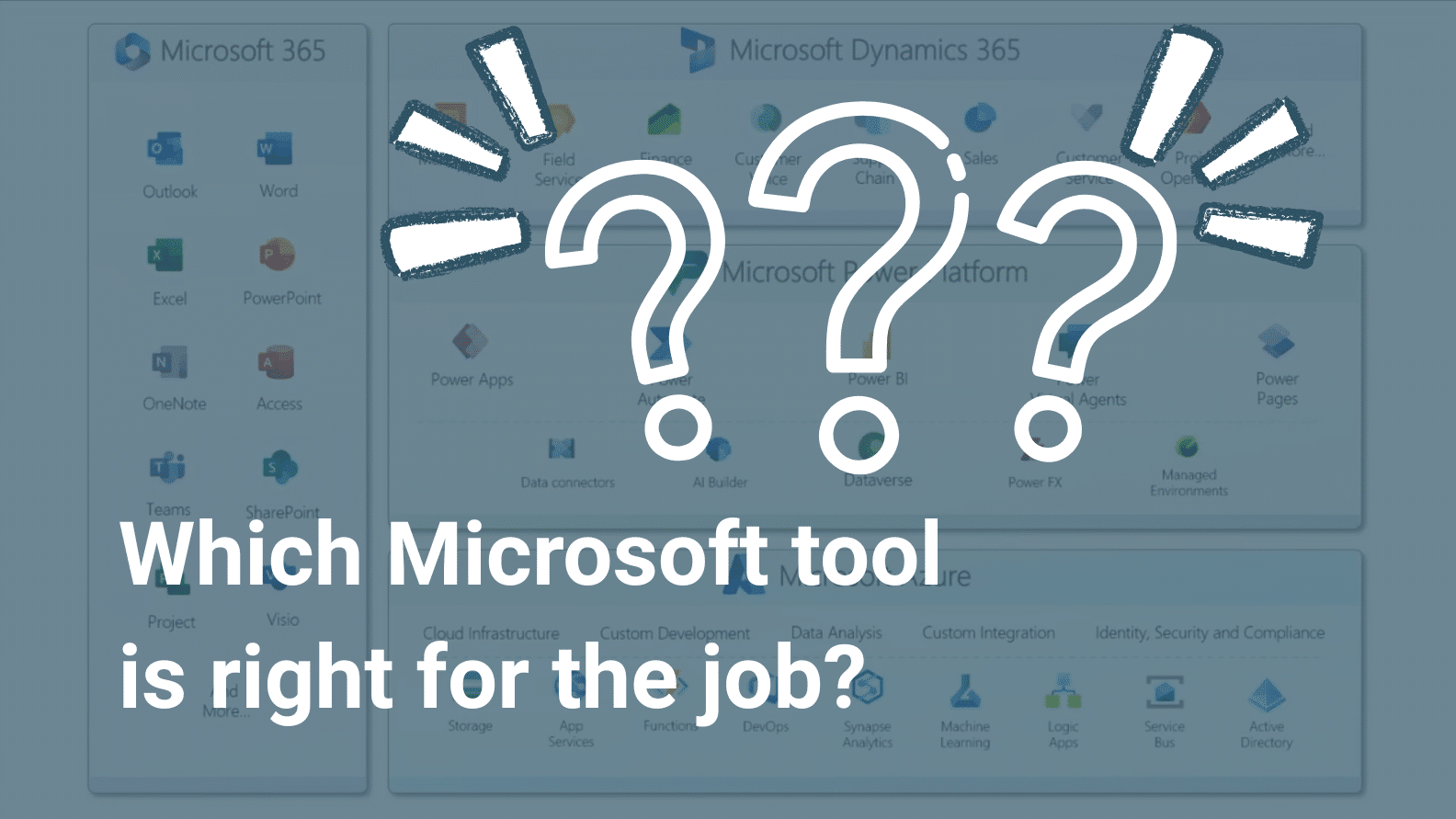
Microsoft’s technology stack has undergone a radical transformation, from a handful of productivity apps to a sprawling, AI-powered ecosystem that […]
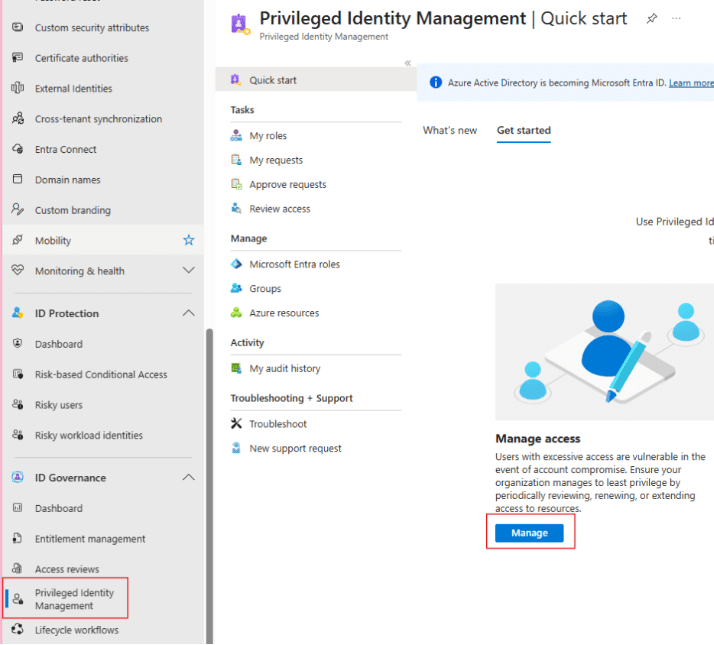
What is Microsoft Entra Privileged Identity Management (PIM)? Microsoft Entra PIM is a security feature within Microsoft Entra ID (formerly […]

As someone who helps onboard new team members and troubleshoot tech issues daily, I’ve seen firsthand how small habits can […]
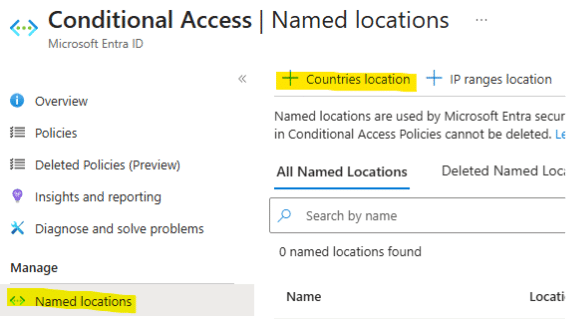
The Role of Conditional Access When it comes to securing your organization’s data, every layer counts. Conditional Access policies give […]

In the food industry, data is just as valuable as your products—and just as vulnerable. Implementing strong cybersecurity in your […]
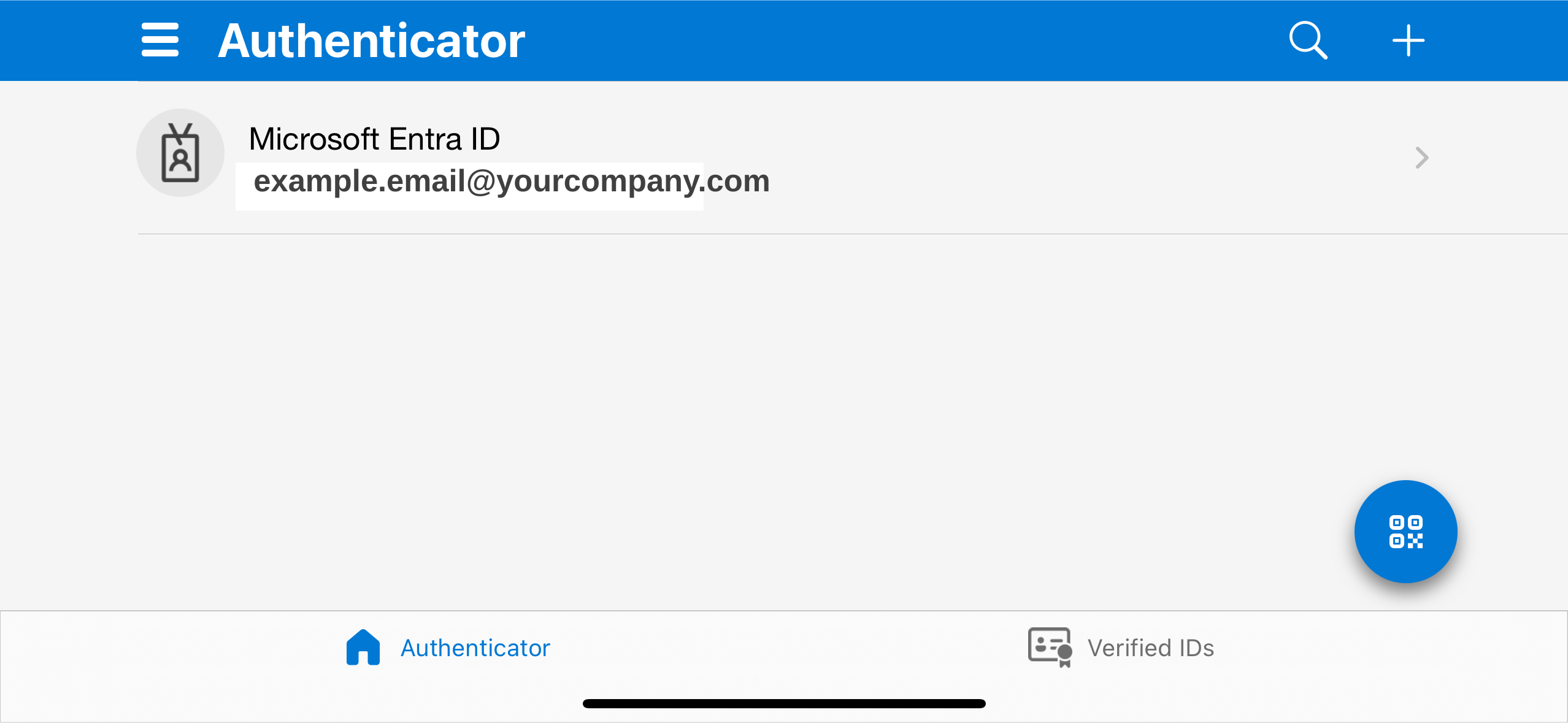
As of September 2025, Microsoft Authenticator in iOS will back up and restore using Apple iCloud + iCloud Keychain, and […]
If your business uses Microsoft technologies, you’ve probably wondered when to seek support from your partner and when to contact […]
If you’ve ever submitted a support request and felt like it disappeared into the digital void, we hear you. As […]

Cyber threats are constantly evolving and becoming more sophisticated. This can lead not only to an increased number of cyber […]
It’s our mission to help clients win. We’d love to talk to you about the right business solutions to help you achieve your goals.