How to Create a Passkey in Microsoft Authenticator
Cyber threats are constantly evolving and becoming more sophisticated. This can lead not only to an increased number of cyber threats, but also to a complicated number of security hoops for your team to jump through.
Fortunately, creating passkeys in Microsoft Authenticator is a straightforward and secure alternative. This replaced traditional passwords with assigned credentials that offer a quick and seamless sign-in experience that is user-friendly and highly resistant to phishing and other cyber attacks.
In this blog, we will show you how to create passkeys in Microsoft Authenticator so you and your team can elevate your security strategy without the headache of password overload.
What are Passkeys in Microsoft Authenticator?
A Passkey is a modern, more secure way to sign in to applications and websites without the need to remember a password. Passkeys use cryptographic keys that are tied to your device to provide authentication. The digital credential is stored securely on your device and uses public-key cryptography to authenticate you. This method is resistant to phishing, password leaks, and brute-force attacks.
Why should I configure Microsoft Authenticator Passkeys?
By adopting Passkeys via the Microsoft Authenticator application, you can:
- Reduce the financial and technical burden of password management
- Provide your users will have a more streamlined sign-in process
- Increase your security against password-based attacks
- Securely store the protected passkey by biometrics or PIN
- Improve your security posture with no additional hardware cost
How You Can Create a Passkey
Once you have Passkey registration configured in your tenant users will be able to follow these steps:
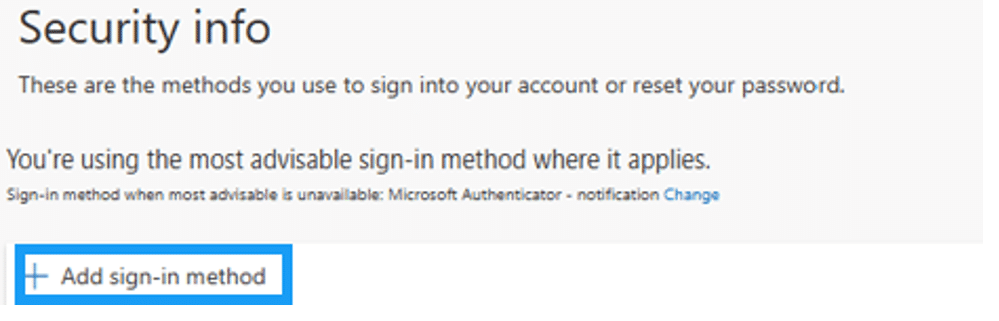
1. Go to My Account and under Security info click on “UPDATE INFO”
2. Click on “Add sign-in method”
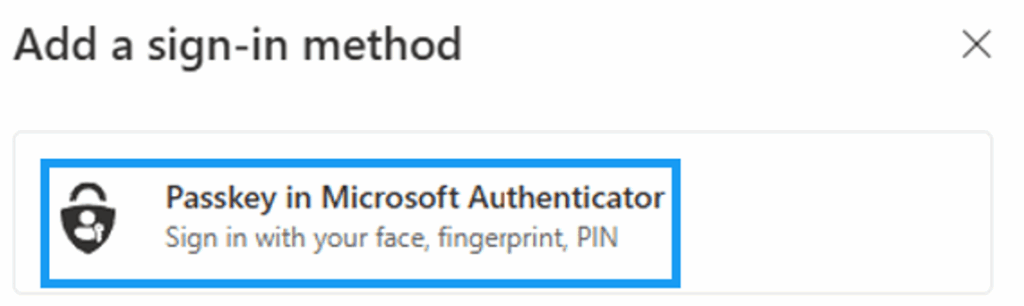
3. Select “Passkey in Microsoft Authenticator”
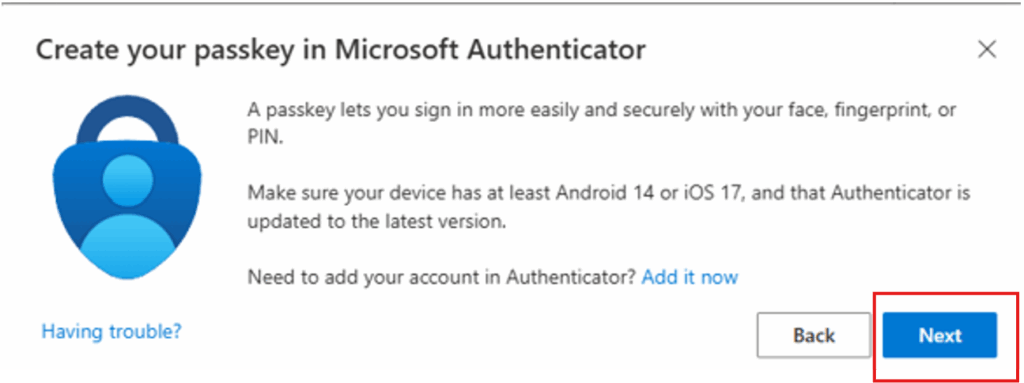
4. Note you need to have the authenticator app and at least Android 14 or iOS 17
You can't create passkeys unless you have these systems. Click “Next” if your device meets this criterion
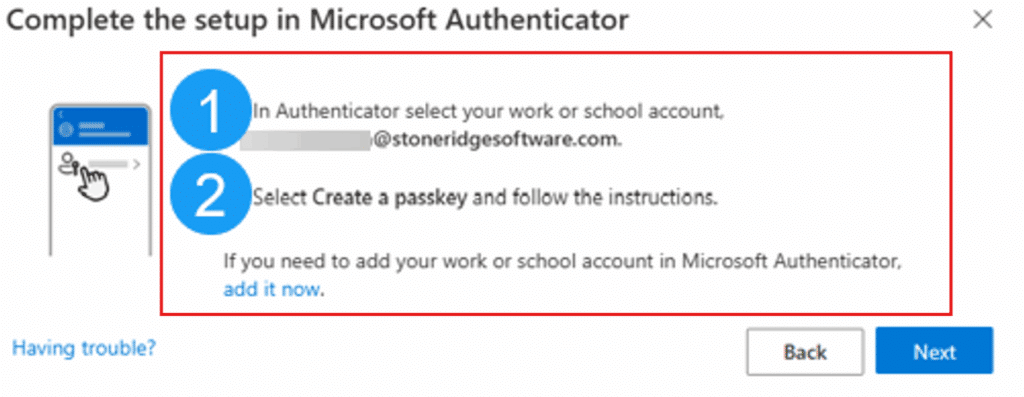
5. Open your authenticator app and follow the instructions before clicking “Next”
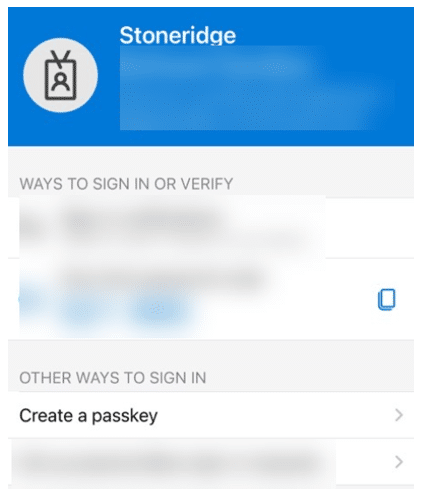
6. From your authenticator app you will see these options:
When you click on your account, click “Create a passkey”.
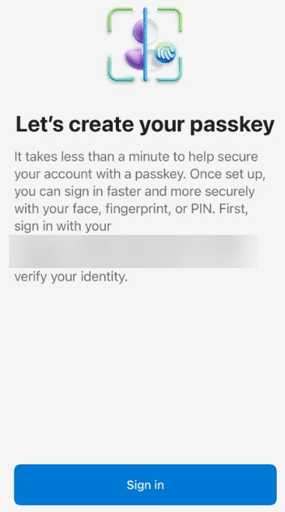
7. Click “Sign In” to create your passkey
This will require your password and MFA.
8. Note your password autofill will have to be turned on for the authenticator app
This means if you already have an autofill you will have to select the correct application to use when prompted for credentials.
9. On your next sign in you will pick your account or fill in your account
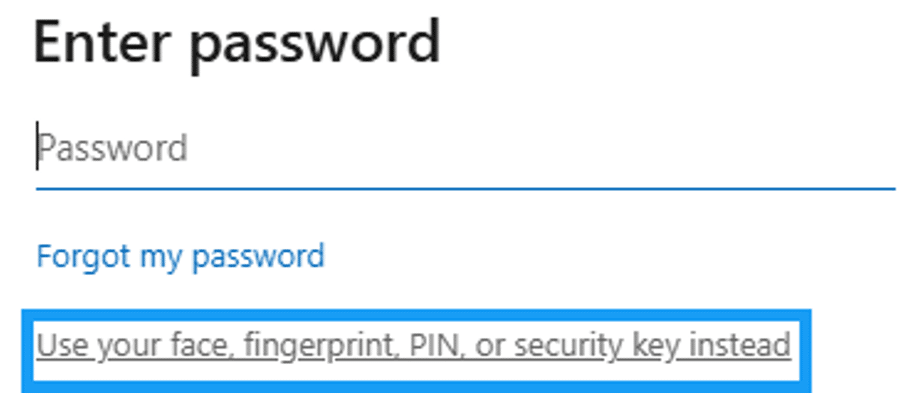
10. Instead of entering your password, select “Use your face, fingerprint, PIN, or security key instead”
11. Sign in with your passkey by choosing “iPhone, iPad, or Android device”
Then, click “Next” (Note the experience will only be steps 11 and 12 after your first sign in).
12. You will need your Bluetooth turned on for both devices
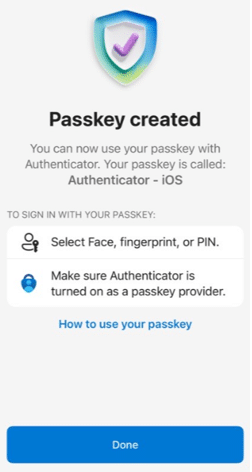
Then, use your camera to scan the QR code. The passkey will be confirmed, and you will be signed in.
Benefits of Microsoft Authenticator Passkeys
- User Experience – No longer need to enter password, just open camera app.
- Bluetooth forces proximity to device
- Private key only on the mobile device provides phishing resistance
- Enumerates details of the passkey request (see step 12 screenshot)
- Biometric Integration
Drawbacks:
While passkeys are high effective, there are a few things you should keep in mind before creating them for your environment:
- You will have to have Bluetooth enabled
- You will have to select the correct credential manager if you have more than one
- Some processes don’t support Passkeys
Always test new configurations before making permanent changes. For example, passkeys can be configured to be an option for users without removing your current process while testing impact.
How the Stoneridge Team Can Help
Every tenant and user base are different. The Stoneridge team can help:
- Configure a custom passkey adoption strategy
- Implement authentication method requirements
- Build conditional access policies to enhance security across your organization
Our team is happy to answer questions, talk through your goals, and guide you through the next steps, at your pace.
Reach out to us to start the conversation.
Under the terms of this license, you are authorized to share and redistribute the content across various mediums, subject to adherence to the specified conditions: you must provide proper attribution to Stoneridge as the original creator in a manner that does not imply their endorsement of your use, the material is to be utilized solely for non-commercial purposes, and alterations, modifications, or derivative works based on the original material are strictly prohibited.
Responsibility rests with the licensee to ensure that their use of the material does not violate any other rights.