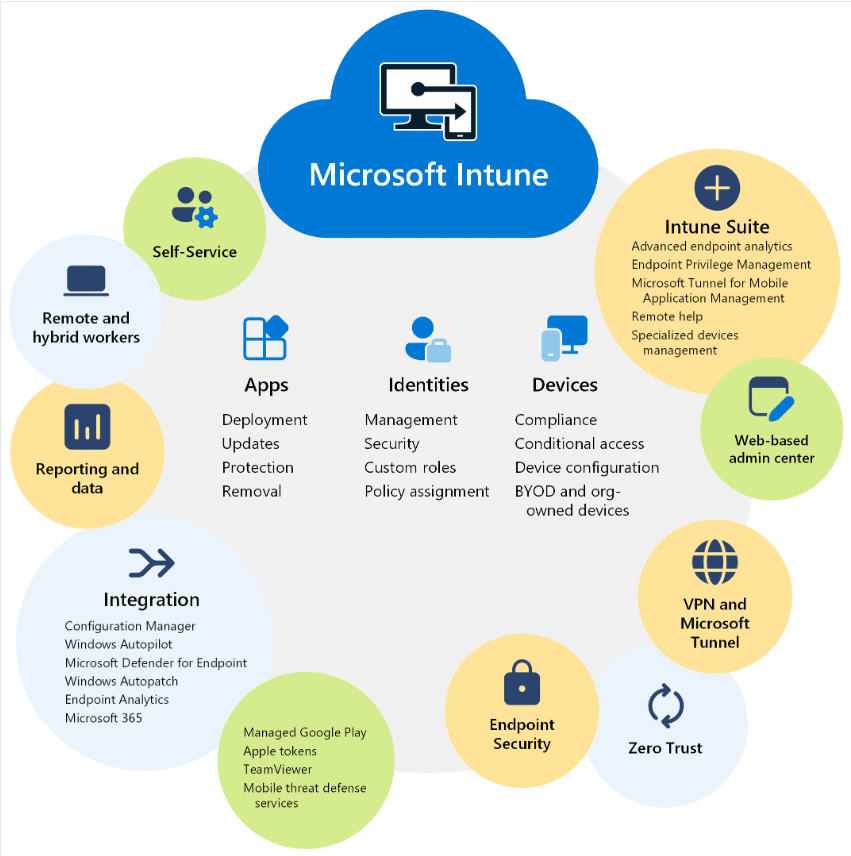
How to Manage Identity and Access Strategies with Microsoft Intune
Microsoft Intune is instrumental in establishing a solid Microsoft Cloud security strategy, simplifying what can often be a time-consuming process.
Securing your data and environment on the Cloud is a big process that requires a lot of work internally. While that might seem daunting, it also leads to enhanced security and opens you to a vast swath of new security tools and applications you can use to protect your organization.
Microsoft Intune: A Key Part of the Cloud Security Ecosystem
While Microsoft Intune isn’t the be-all-end-all of Cloud security, it’s a very important aspect. When securing your environment, you need to think about the specific aspects of your team and even people outside of your organization. Consider some of these questions:
- What data does each member of your team need access to?
- What applications do team members use?
- What devices do they operate on? Are there differences between mobile devices? Laptops? Tablets?
- How will you manage security and access for guests, contractors, or others outside of your organization?
- How do you want to handle multi-factor authentication or login authorization?
As an endpoint management tool, Microsoft Intune can help you answer these questions and with the help of a Cloud Security partner like Stoneridge Software, it can give you a comprehensive strategy that covers every corner of your organization.
Let’s dig into Microsoft Intune and highlight some of the main features and functionalities you can use.
What is Microsoft Intune?
Microsoft Intune is a cloud-based identity and access management solution that enables efficient management of devices across your organization. Whether it’s Windows PCs, Macs, iOS, or Android devices, Intune provides a unified platform for configuration, security, and app management.
Intune provides a unified platform for configuration, security, and app management. Here are some key benefits:
Unified Management:
Intune streamlines device management, allowing you to handle everything from a single console. This eliminates the need to implement multiple tools and the tedious task of switching back and forth between them.
Whether it’s provisioning new devices, enforcing policies, or troubleshooting issues, Intune simplifies the process.
Security Enhancements:
Protect your devices and data with robust security features like:
- Conditional Access: Set access rules based on user context, device health, and location.
- Encryption: Safeguard sensitive data at rest and in transit.
- Threat Detection: Intune keeps an eye out for and monitors suspicious activity.
Boost Productivity:
Intune ensures seamless access to corporate resources, apps, and data. Your employees can work securely from anywhere, anytime.
No more productivity roadblocks due to device misconfigurations or security hurdles.
Automated Deployments:
Set up new devices effortlessly. Intune automates device enrollment, configuration, and app deployment.
Say hello to zero-touch deployments and goodbye to manual intervention headaches.
Insights and Analytics:
Gain visibility into device health, compliance, and usage patterns. These data-driven decisions lead to better security posture and optimized device performance.
How Does Microsoft Intune Work?
From a service perspective, Intune relies on Microsoft Entra ID (Azure AD) for identity storage and permissions. The Intune admin center serves as the central hub for managing these tasks, designed specifically for endpoint management. Remember that your identities are necessary to create both security groups and populate the devices for management.
If you want to ensure your identities are where you need them to be and secured properly, be sure to audit them before new enablement that will provide access to your data.
Leveraging Existing Users and Groups
Intune simplifies the process of managing users and groups:
- On-Premises Environment: If you’re transitioning from an on-premises Active Directory, Intune seamlessly integrates. You can update users and groups using any domain controller in the domain.
- Intune will work in tandem with your on-premises devices and Microsoft Microsoft System Center Configuration Manager (SCCM)
- The admin center provides a unified location for managing users and groups. Admins simply sign in with their Intune administrator account.
Deploying Apps Your Organizations Uses
Thoughtful app management enhances productivity and security. Explore Intune’s features and align them with your organization’s needs.
For more details, visit the Microsoft Learn website.
Remember, Zero Trust is about continuous vigilance and proactive security. Intune empowers organizations to embrace these principles and protect their assets effectively.
Key Takeaways for Microsoft Intune
When exploring what Microsoft Intune can do for your security strategy, consider these things:
- Cloud security is always evolving, stay tuned for more updates and insights on Microsoft Intune and other Microsoft Cloud solutions.
- Intune as part of the Endpoint Manager suite is part of a larger conversation of Zero Trust enablement. Trust, but verify!
- Always plan your deployments for the least permissive access. You can always open access if you need to, which is easier than closing access in hindsight.
- Assume Breach – Cyber-attacks will happen, Intune can help you:
- Minimize the blast radius
- Segment access
- Implement Endpoint Privilege Management (EPM) to run users as standard users while allowing elevated privilege tasks for those who need it.
- As part of a larger security and access framework, Intune will also help keep consistency across devices, applications, and user behaviors. Even if a device is lost, your data can be protected!
- “Don’t set it and forget it. Define it and refine it.” Your cybersecurity systems and protocols need constant monitoring and updating.
Stoneridge Software is Your Cloud Security Partner
Stoneridge’s cloud consulting team can help you implement Intune and take advantage of all the other aspects of Microsoft Cloud security. Ensuring you have a comprehensive and effective cybersecurity strategy that gives you and your team peace of mind is one of the most vital things you can do. We can help you implement these tools and use them to protect your environment and the data in it.
Reach out to our team to learn more.
Under the terms of this license, you are authorized to share and redistribute the content across various mediums, subject to adherence to the specified conditions: you must provide proper attribution to Stoneridge as the original creator in a manner that does not imply their endorsement of your use, the material is to be utilized solely for non-commercial purposes, and alterations, modifications, or derivative works based on the original material are strictly prohibited.
Responsibility rests with the licensee to ensure that their use of the material does not violate any other rights.