Understanding Permission Sets in Dynamics 365 Business Central
Managing permission sets in Dynamics 365 Business Central can be complex, especially for organizations with varied user roles and security requirements.
This blog will dive into the intricacies of permission sets and security within Business Central.
What Are Permissions in Business Central?
In Business Central, permissions control what a user can access within the system. Unlike roles, which are designed to configure the user interface appearance and make workflows more efficient, permissions determine the level of access users have to different data and functions.
It's important to note that permissions and roles are not the same. While roles enhance the user experience by adjusting what appears on the screen, permissions define whether users can view, modify, or delete data within the system. Permissions are crucial in safeguarding sensitive information and maintaining system security.
Understanding User Cards and Permission Sets
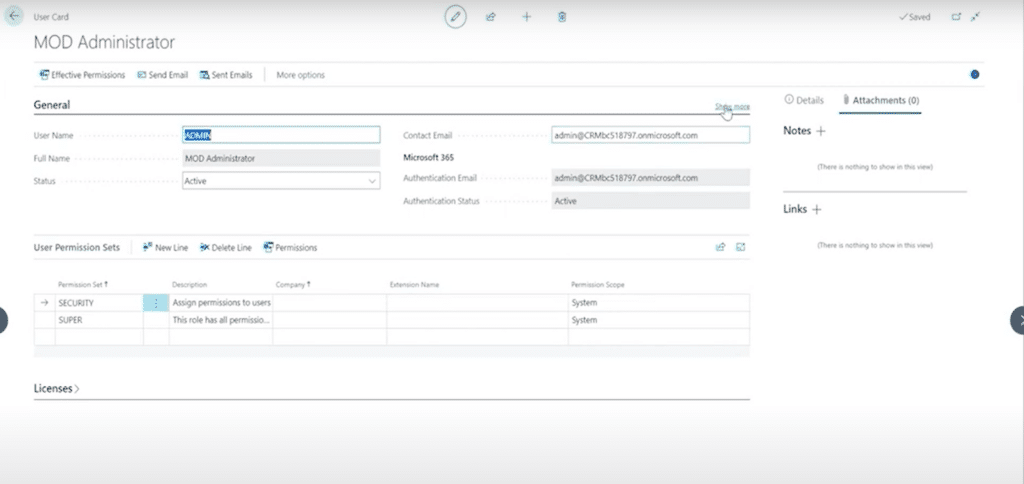
User cards are a visual view of a user profile within Business Central. This card includes several tabs like "General," where basic information such as the user’s name and status (active or inactive) is listed. However, the critical section is the Permission Sets tab, where administrators can configure the user’s access rights.
For example, an administrator might have permission sets such as “Super,” which grant full control over the system. This permission set allow them to view and edit any part of Business Central. Administrators can also restrict access to specific companies, even when users have wide-reaching permissions.
Permission Sets Breakdown
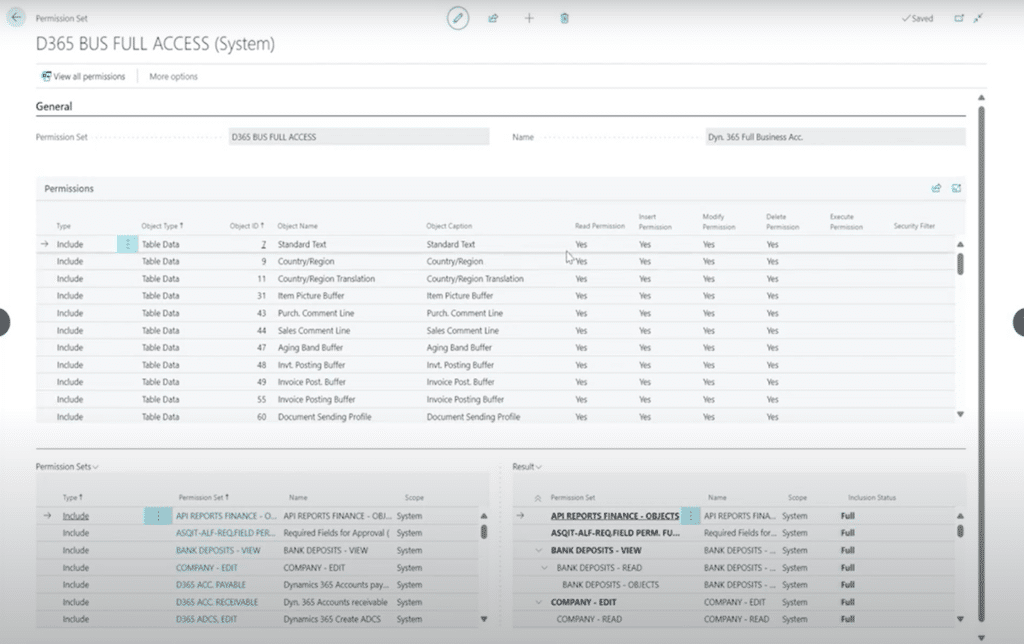
In Business Central, a permission set is a collection of permissions tied to specific tables or actions within the system. You can inspect permission sets by viewing the Permission Set List, which contains pre-configured permission sets available in Business Central.
Each permission set includes different types of permissions:
- Read: View the data without making changes.
- Insert: Add new data entries.
- Modify: Edit existing data.
- Delete: Remove data.
- Security Filer: Filter Users view only specific data.
Two good examples of this are:
- The Assembly View permission set: This allows users to view assembly orders.
- The Assembly Edit permission set: This one enables modifications.
These sets can be combined to give users tailored access to various parts of the system.
Nesting Permission Sets
Nesting permission sets include other permission sets. This means when you assign a high-level permission set like D365 Business Full Access, it will encompass multiple other sets, thereby granting a user comprehensive access to the entire system. Nesting allows you to Exclude specific areas you don’t want people to access.
The Page and Table Relationship
One of the key concepts you need to understand is the relationship between pages and tables in Business Central. A page is what the user interacts with on the screen, while a table holds the data behind the scenes. For instance, the Sales Order Page is linked to the Sales Header Table and Sales Line Table.
By understanding this structure, administrators can configure permissions more effectively. If a user needs to work with sales orders, they require access to the table and the corresponding page. Without the proper permissions, users will encounter errors or be blocked from performing important tasks.
Creating Custom Permission Sets
While Business Central offers a wide range of system-defined permission sets, administrators can create their own user-defined permission sets to tailor access further. This process involves selecting specific tables and configuring the necessary read, insert, modify, or delete permissions.
Although creating custom permission sets requires a deep understanding of the system’s structure, it provides an opportunity to lock down specific areas while ensuring users have the permissions they need to perform their job functions.
Balancing Security with Functionality
Finding the right balance between security and usability is another key thing to sort out when managing permission sets. Businesses should carefully consider how much security they truly need. For instance, a publicly traded company with strict compliance requirements may need tight controls over who can access financial data. In contrast, a small family-run business might not require stringent security measures and can allow employees broader access.
Security by Obscurity
This is a process where administrators grant full access to users but prevent them from seeing certain parts of the system. This approach allows users to perform their tasks without being overwhelmed by irrelevant or sensitive data. Removing specific pages from a user's view helps create a more streamlined and secure experience.
Common Pitfalls: Over-Assigning Permissions
It's important to never over-assign permissions because it gives users more access than they need. In many cases, administrators assign users the D365 Business Full Access or D365 Business Premium permission sets. This allows them to perform almost every task in the system, including viewing sensitive financial information.
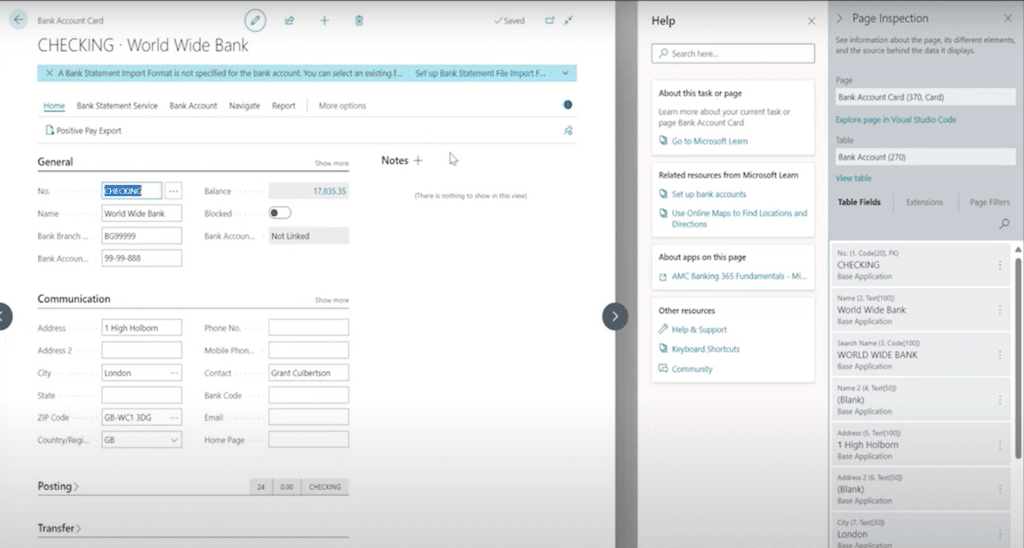
Users with excessive permissions can inadvertently access data like bank accounts. By using the Help tool and inspecting pages, users can see and access data stored in specific tables, like bank account data in Table 270. Companies need to be cautious about what data is accessible to prevent unnecessary risks.
Key Takeaways for Managing Permissions
To wrap up, let's go over some of the key things you need to know about permissions in Business Central:
- Understand the difference between roles and permissions: Roles shape the user interface, while permissions control access to data.
- Review and tailor permission sets: Avoid over-assigning permissions, as it can lead to users accessing sensitive areas of the system containing information they don't need to access.
- Nested permissions: Nested Permissions can be used to restrict access to certain areas of the system.
- Consider creating custom permission sets: For more precise control over user access, you can create custom permission sets and tailor them to your team members.
- Balance security with business needs: The level of security should align with the organization’s structure and compliance requirements.
Get in touch with Stoneridge to Learn More About Managing Business Central
Reach out to our experts today to gain more insight into effectively running Business Central. Our experts can help you establish a permissions guideline for your organization and help you identify additional ways to optimize your environment.
Under the terms of this license, you are authorized to share and redistribute the content across various mediums, subject to adherence to the specified conditions: you must provide proper attribution to Stoneridge as the original creator in a manner that does not imply their endorsement of your use, the material is to be utilized solely for non-commercial purposes, and alterations, modifications, or derivative works based on the original material are strictly prohibited.
Responsibility rests with the licensee to ensure that their use of the material does not violate any other rights.