Upcoming Changes to Microsoft’s Default Application Consent Settings
Beginning mid-July and continuing through August 2025, Microsoft is rolling out updates to several default settings across Microsoft 365 tenants. One key change involves how users grant permissions to third-party applications—a process known as application consent. These updates are designed to strengthen security by limiting automatic approval of high-risk permissions, particularly those involving access to user files or SharePoint sites.
If your organization relies on cloud applications, it’s important to understand what’s changing and how it might impact users and admins. This post outlines what application consent is, how the new defaults will work, and what steps you may need to take to align your organization’s environment with the updated policies.
What is Application Consent?
Application consent is the process by which a user grants permission to applications to access their data or perform actions on their behalf. This could include access to contacts, emails, or other personal data to provide enhanced functionality. In some cases, users may see a prompt asking them to grant these permissions; in others, an administrator must approve the request before access is granted. Below is an example of the standard application consent prompt users may encounter:
Note: These changes only apply to tenants without a custom policy in place and where an application requests access to user files or sites.
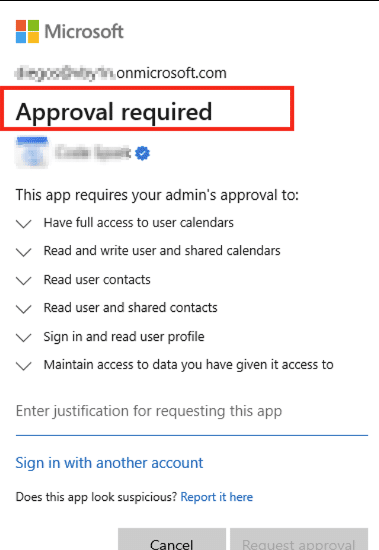
If an admin consent policy is in place, non-privileged users will need to submit a request for administrator review and approval, as shown here:
What is Changing?
With respect to the timeline above, Microsoft-managed Application Consent Policies will be enabled. These policies will require administrator consent for any third-party application requesting access to the following permissions:
- files.read.all
- files.readwrite.all
- sites.read.all
- sites.readwrite.all
This means users will no longer be able to approve these permissions on their own unless your organization has already implemented a custom app consent policy.
Why is Microsoft Making this Change?
Data access is a common attack vector for malicious applications. By requiring administrator approval for high-risk permissions, Microsoft aims to reduce the chance of unauthorized data exposure. According to IBM's “Cost of a Data Breach Report 2024,” the global average cost of a data breach was $4.9M USD, highlighting the importance of proactive access control and oversight.
How is Application Consent Exploited?
One of the most common tactics used by threat actors is consent phishing. This involves seemingly legitimate applications that trick users into granting permissions to data and performing actions without needing their credentials. With elevated permissions, these apps can exfiltrate data or carry out unauthorized actions.
How the Stoneridge Team Can Help
Although Microsoft’s current deployment is mandatory, every tenant is different. The Stoneridge team can help:
- Configure custom app consent permission review and acceptance strategy
- Implement custom administrator workflows
- Build conditional access policies to enhance security across your organization
Our team is happy to answer questions, talk through your goals, and guide you through the next steps, at your pace. Reach out to us to start the conversation.
Under the terms of this license, you are authorized to share and redistribute the content across various mediums, subject to adherence to the specified conditions: you must provide proper attribution to Stoneridge as the original creator in a manner that does not imply their endorsement of your use, the material is to be utilized solely for non-commercial purposes, and alterations, modifications, or derivative works based on the original material are strictly prohibited.
Responsibility rests with the licensee to ensure that their use of the material does not violate any other rights.